Two weeks ago, Equifax – one of the country’s biggest credit reporting agencies – announced that its systems were hacked by cybercriminals, exposing the Social Security numbers, birth dates, addresses, and driver's license numbers of 143 million Americans. Unfortunately, this huge data breach was not unprecedented. The personal information for 1 billion Yahoo users and 145 million eBay users was exposed in 2013 and 2014, respectively.
The reality is that our private information is more vulnerable than ever today due to our heavy reliance on technology – which has a lot of people concerned about their 401(k)’s vulnerability to cybertheft. If you’re one of these people, I have some good news. Most 401(k) plans are more resilient to cybertheft than personal bank accounts or IRAs due to their fiduciary hierarchy - which requires the employer to approve any cash disbursements - generally, plan asset transfers or participant distributions.
However, not all 401(k) plans include this important asset safeguard. Some employers delegate the two fiduciary roles that approve cash disbursements to their 401(k) provider. In my view, this outsourcing of fiduciary authority makes a 401(k) plan more vulnerable to cybertheft.
The 401(k) plan fiduciary hierarchy
The basic fiduciary hierarchy applicable to all 401k plans can be found below. It includes both fiduciary and ministerial (non-fiduciary) roles. The blue boxes indicate roles generally filled by the employer, while the other boxes indicate roles filled by professional 401(k) providers. However, it’s possible for an employer to delegate all of these roles to a 401(k) provider.
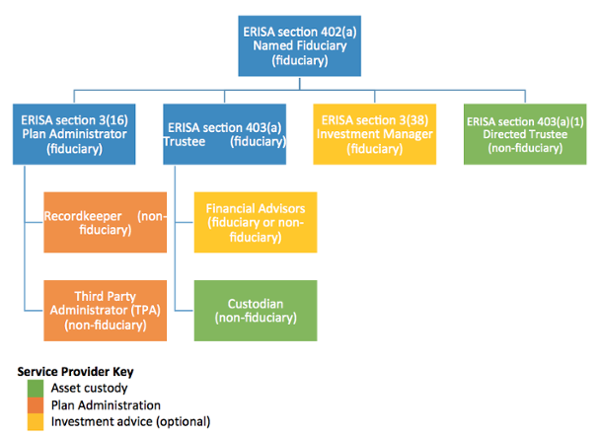
Fiduciary roles that can easily thwart cybertheft
Within the 401(k) plan fiduciary hierarchy, there are only two fiduciary roles that can direct the Custodian to transfer or distribute plan assets:
- ERISA 403(a) Trustee – is named in a 401k plan or trust document and has exclusive authority and discretion to manage and control plan assets.
- ERISA 3(16) Plan Administrator – is basically responsible for any fiduciary responsibility not assumed by the ERISA 403(a) Trustee.
These roles are often a 401(k) plan’s last line of defense when a cybercriminal attempts to steal its assets.
403(a) Trustee
In 2013, Matthew Hutcheson was sentenced to over 17 Years in prison for stealing $2 million from an “open” Multiple Employer Plan (MEP) - a type of 401(k) plan co-sponsored by potentially hundreds of unrelated employers. How did he do it? The MEP co-sponsors delegated their 403(a) Trustee authority to Hutcheson – the MEP provider and lead plan sponsor. This authority allowed Hutcheson to transfer MEP assets away from the Custodian without employer approval.
I don’t think an employer should ever delegate their 403(a) Trustee authority – which is only used as part of a 401(k) provider change generally – because their independent approval of plan asset transfers makes theft (cyber or otherwise) less likely. The good news? This delegation is easily avoidable by avoiding MEPs – generally, the only type of 401(k) plan that forces the delegation of 403(a) Trustee authority.
3(16) Plan Administrator
Today, some 401(k) providers try to differentiate themselves by assuming certain basic 3(16) Plan Administrator fiduciary responsibilities - like approving participant distributions/loans and signing the Form 5500 – from the employer. These “3(16) services” are supposed to lower the employer’s 401(k) fiduciary liability, but I think they do the opposite by replacing easy-to-meet fiduciary responsibilities with a more difficult responsibility to monitor a 401(k) provider with fiduciary (discretionary) authority.
I also think 3(16) services make 401(k) account cybertheft easier. Employers – especially small employers – have a closer personal relationship with their 401(k) plan participants than a 401(k) provider. This personal relationship can make it easier to deny suspicious distribution or loan requests.
Giving up fiduciary responsibilities can make cybertheft more likely
Today, there are trillions of dollars invested in 401(k) plans nationwide – which makes these plans an attractive target for cybercriminals. The good news is that most 401(k) plans are more resilient to cybertheft than other types of financial accounts because the employer must approve any cash disbursements from their plan.
However, some 401(k) providers offer outsourced 403(a) Trustee and 3(16) Plan Administrator services, which make them the last line of defense against cybertheft. I think these services make 401(k) cybertheft easier because they remove the employer’s independent approval of plan asset transfers or participant distributions.